SSL encryption
Secure Sockets Layer: This name stands behind the far more common designation SSL, which is now also known as TLS (Transport Layer Security). It refers to an encryption protocol that aims to enable secure data transmission in networks with a key. Specifically, SSL is a hybrid encryption protocol. This means that a combination of symmetric and asymmetric encryption is used. In the first step, a so-called session key is created (random but symmetric). Based on this session key, the data is secured according to the symmetric principle. Subsequently, the session key is asymmetrically encrypted with the recipient's session key.
Due to the hybrid encryption method with SSL, the so-called key distribution problem in data exchange is solved. While symmetric methods are very fast, exchange partners must agree on a common secret key, for which a secure communication channel must be available. Asymmetric methods solve this problem. However, they are very slow with large amounts of data and are actually only suitable for small amounts. The hybrid form in Secure Sockets Layer ensures that large amounts of data can be transmitted quickly and encrypted—the positive properties of symmetric and asymmetric methods are thus retained.
With the SSL certificate, one prevents criminals from being able to read or alter personal information, thereby increasing IT security.
Layer system
As the term Layer in Secure Sockets Layer reveals, these are layers of the transmission protocol. The original TCP/IP protocol initially covered at least four layers. However, secure connections could not be guaranteed with it. So, two more layers were added:
SSL Record Protocol
SSL Handshake Protocol
These layers lie between the TCP/IP responsibilities and the applications. The good thing is that applications like browsers do not notice the two additional layers of SSL certificates. An SSL certificate, therefore, does not require changes from applications or transport protocols.
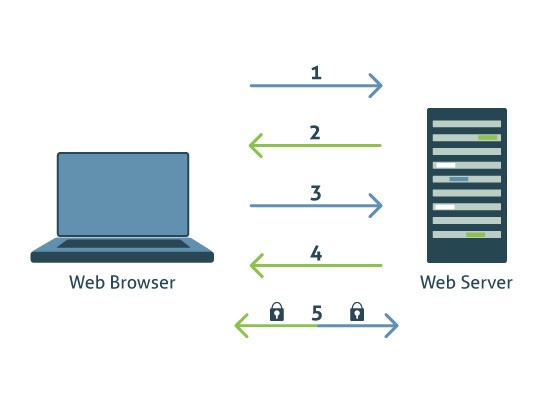
SSL – Secure Sockets Layer in practice
As a rule, the procedure first developed in 1994 is used with HTTPS, a wiretap-proof communication protocol seen among other things in online banking or in email programs. When data exchange occurs, the client establishes a connection to the server. Usually, web hosts offer so-called SSL proxies in this context - special servers that secure websites via an SSL certificate and are hosted externally by other websites under the same IP address. The server authenticates itself in turn through a certificate, which is verified by the client. It is also possible for the client and server to verify each other through a certificate. Subsequently, a common secret key is randomly created to secure the data via a symmetric encryption method.
In practice, however, it should be noted that with SSL, data is only securely transmitted to the server. For the data to securely reach the recipient, the recipient must also retrieve the information securely using SSL encryption. Therefore, there is no 100% guarantee that the data will actually reach the recipient securely. Because encryption is only possible between two stations, but data exchange can run over several, security gaps arise, which, as practice shows, are also regularly uncovered.
What is not secured by SSL
With the SSL protocol, the transmission between a domain on a server and the domain visitor is secured. For example, a credit card number cannot be read during the SSL encryption on the website. However, the best certificate and key cannot influence what happens to the securely transmitted data afterward. Secure Sockets Layer therefore does not protect against irresponsible handling of sensitive data by the data recipients. Therefore, one should always pay attention to how a shop, for example, handles the data in the further course.